-
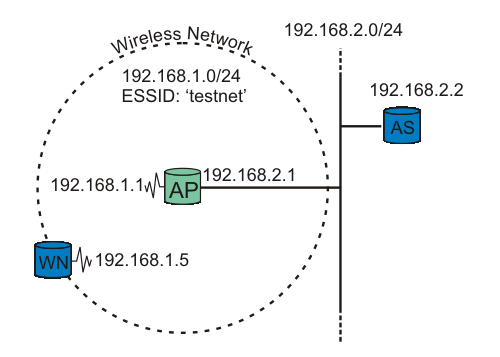
- Bizim deneme sistemimiz iki düğüm ve bir Erişim Noktasından (AP) oluşur. Bir düğüm İstemci (WN) gibi, diğeri RADIUS (AS) çalıştıran artalan Kimlik Kanıtlama Sunucusu gibi davranır. Erişim Noktası Kimlik Kanıtlayıcıdır. Açıklama için Şekil 3.7'ye bakınız

Önemli Erişim Noktasının Kimlik Kanıtlama Sunucusuna erişebilmesi (ping) ve tam tersi son derece önemlidir!
- Yönerge 3.5. bazı denemeler
- RADIUS sunucu hata ayıklama kipinde başlatılır. Bu çok miktarda hata ayıklama bilgisi üretir. Önemli noktalar aşağıdadır:
# radiusd -X Starting - reading configuration files ... reread_config: radiusd.conf'u okuyor Config: including file: /usr/local/etc/raddb/proxy.conf Config: including file: /usr/local/etc/raddb/clients.conf Config: including file: /usr/local/etc/raddb/snmp.conf Config: including file: /usr/local/etc/raddb/eap.conf Config: including file: /usr/local/etc/raddb/sql.conf ...... Module: Loaded MS-CHAP mschap: use_mppe = yes mschap: require_encryption = no mschap: require_strong = no mschap: with_ntdomain_hack = no mschap: passwd = "(null)" mschap: authtype = "MS-CHAP" mschap: ntlm_auth = "(null)" Module: Instantiated mschap (mschap) ...... Module: Loaded eap eap: default_eap_type = "peap" eap: timer_expire = 60 eap: ignore_unknown_eap_types = no eap: cisco_accounting_username_bug = no rlm_eap: Loaded and initialized type md5 tls: rsa_key_exchange = no tls: dh_key_exchange = yes tls: rsa_key_length = 512 tls: dh_key_length = 512 tls: verify_depth = 0 tls: CA_path = "(null)" tls: pem_file_type = yes tls: private_key_file = "/usr/local/etc/raddb/certs/cert-srv.pem" tls: certificate_file = "/usr/local/etc/raddb/certs/cert-srv.pem" tls: CA_file = "/usr/local/etc/raddb/certs/demoCA/cacert.pem" tls: private_key_password = "SecretKeyPass77" tls: dh_file = "/usr/local/etc/raddb/certs/dh" tls: random_file = "/usr/local/etc/raddb/certs/random" tls: fragment_size = 1024 tls: include_length = yes tls: check_crl = no tls: check_cert_cn = "(null)" rlm_eap: Loaded and initialized type tls peap: default_eap_type = "mschapv2" peap: copy_request_to_tunnel = no peap: use_tunneled_reply = no peap: proxy_tunneled_request_as_eap = yes rlm_eap: Loaded and initialized type peap mschapv2: with_ntdomain_hack = no rlm_eap: Loaded and initialized type mschapv2 Module: Instantiated eap (eap) ...... Module: Loaded files files: usersfile = "/usr/local/etc/raddb/users" ...... Module: Instantiated radutmp (radutmp) Listening on authentication *:1812 Listening on accounting *:1813 İstekleri işlemek için hazır.
Radius sunucu istekleri işlemek için artık hazır!En ilginç çıktı yukarıda gösterilmiştir. Eğer en son satırın yerine her hangi bir hata iletisi alıyorsanız yapılandırmaya (yukarıda) dikkatli bir şekilde bakın. - Şimdi İstemci kimlik doğrulaması için hazır. Xsupplicant'ı hata ayıklama kipinde başlatın. İki başlatma betiği tarafından üretilen çıktıyı göreceğimize dikkat edin: startup.sh ve startup2.sh.
# xsupplicant -c /usr/local/etc/1x/1x.conf -i eth0 -d 6 /etc/1x/startup.sh: işlem başlatılıyor /etc/1x/startup.sh: işlem tamam /etc/1x/startup2.sh: işlem başlatılıyor /etc/1x/startup2.sh: işlem tamam
- Aynı zamanda RADIUS sunucu da çok miktarda çıktı üretiyor olacak. Başlıca bilgiler aşağıda gösterilmiştir:
...... rlm_eap: Request found, released from the list rlm_eap: EAP/peap rlm_eap: processing type peap rlm_eap_peap: Authenticate rlm_eap_tls: processing TLS eaptls_verify returned 7 rlm_eap_tls: Done initial handshake eaptls_process returned 7 rlm_eap_peap: EAPTLS_OK rlm_eap_peap: Session established. Decoding tunneled attributes. rlm_eap_peap: Received EAP-TLV response. rlm_eap_peap: Tunneled data is valid. rlm_eap_peap: Success rlm_eap: Freeing handler modcall[authenticate]: module "eap" returns ok for request 8 modcall: group authenticate returns ok for request 8 Login OK: [testuser/<no User-Password attribute>] (from client testnet port 37 cli 0002a56fa08a) Sending Access-Accept of id 8 to 192.168.2.1:1032 MS-MPPE-Recv-Key = 0xf21757b96f52ddaefe084c343778d0082c2c8e12ce18ae10 a79c550ae61a5206 MS-MPPE-Send-Key = 0x5e1321e06a45f7ac9f78fb9d398cab5556bff6c9d003cdf8 161683bfb7e7af18 EAP-Message = 0x030a0004 Message-Authenticator = 0x00000000000000000000000000000000 User-Name = "testuser"
 TLS oturumu başlatılıyor. TLS el sıkışması yapılıyor.
TLS oturumu başlatılıyor. TLS el sıkışması yapılıyor. TLS oturumu (PEAP-şifreli tünel) çalışıyor.
TLS oturumu (PEAP-şifreli tünel) çalışıyor. İstemcinin RADIUS sunucu tarafından başarıyla kimlik kanıtlaması yapılmıştır. "Access-Accept" iletisi gönderilir.
İstemcinin RADIUS sunucu tarafından başarıyla kimlik kanıtlaması yapılmıştır. "Access-Accept" iletisi gönderilir. MS-MPPE-Recv-Key [RFC2548 bölüm 2.4.3], Kimlik Kanıtlayıcıya (erişim noktası) yönelmiş, MPPE Protokolüyle [RFC3078] şifrelenmiş Kimlik Kanıtlayıcı ve Kimlik Kanıtlama Sunucusu arasında paylaşılan sırrı anahtar olarak kullanan Ana Oturum Anahtarını (PMK) içerir. İstemci Anahtar Yönetimi bölümünde tanımlandığı gibi MK'den aynı PMK'yi türetir.
MS-MPPE-Recv-Key [RFC2548 bölüm 2.4.3], Kimlik Kanıtlayıcıya (erişim noktası) yönelmiş, MPPE Protokolüyle [RFC3078] şifrelenmiş Kimlik Kanıtlayıcı ve Kimlik Kanıtlama Sunucusu arasında paylaşılan sırrı anahtar olarak kullanan Ana Oturum Anahtarını (PMK) içerir. İstemci Anahtar Yönetimi bölümünde tanımlandığı gibi MK'den aynı PMK'yi türetir. - Kimlik Kanıtlayıcı (erişim noktası) buna benzer günlük kayıtları gösterebilir:
00:02:16 (Info): Station 0002a56fa08a Associated 00:02:17 (Info): Station=0002a56fa08a User="testuser" EAP-Authenticated
İşte bu! İstemicini artık Erişim Noktasını kullanması için kimlik doğrulaması yapılmış oldu!